In today's interconnected world, securely connecting remote IoT devices through SSH on an Ubuntu server is more crucial than ever. As more organizations rely on IoT networks to streamline operations, ensuring secure communication is paramount. This article will explore how to establish a robust and secure P2P SSH connection for remote IoT devices using an Ubuntu server.
With the rapid growth of IoT devices, security concerns have become a significant challenge. Hackers are constantly seeking vulnerabilities in IoT networks, making it essential to adopt secure practices. By leveraging SSH, a widely trusted protocol, you can safeguard your IoT devices and ensure seamless communication.
This guide will walk you through the process of setting up a secure connection, highlighting best practices, and offering actionable tips to protect your IoT ecosystem. Whether you're a network administrator, developer, or security professional, this article will equip you with the knowledge needed to fortify your remote IoT connections.
- The Rockefeller Family A Legacy Of Wealth Power And Influence
- Edvin Ryding The Rising Star In Music And Beyond
Table of Contents
- Introduction to SSH
- Understanding Remote IoT Connections
- Setting Up an Ubuntu Server
- Configuring SSH for Remote Access
- Securing Your SSH Connection
- P2P SSH Connection for IoT
- Best Practices for Secure Connections
- Troubleshooting Common Issues
- Monitoring and Maintenance
- Conclusion and Next Steps
Introduction to SSH
Secure Shell (SSH) is a cryptographic protocol designed to secure network services over an unsecured network. It provides a secure channel for remote communication, allowing users to execute commands, transfer files, and manage systems securely. SSH is widely used in server administration and IoT environments due to its robust encryption and authentication mechanisms.
SSH operates on port 22 by default and supports various authentication methods, including password-based and public-key authentication. Public-key authentication is highly recommended for securing IoT devices, as it eliminates the risk of brute-force password attacks.
Key Features of SSH
- End-to-end encryption for secure data transmission
- Support for multiple authentication methods
- Compatibility with a wide range of operating systems
- Ability to tunnel other protocols for secure communication
Understanding Remote IoT Connections
Remote IoT connections enable devices to communicate and exchange data over the internet. These connections are essential for monitoring, controlling, and managing IoT devices from a central location. However, securing these connections is critical to prevent unauthorized access and data breaches.
- Mastering Remote Iot P2p Download The Ultimate Guide
- Bruno Mars And The Rumor Does Bruno Mars Have Cancer
IoT devices often operate in unsecured environments, making them vulnerable to cyberattacks. By implementing secure communication protocols like SSH, you can protect your devices and ensure the integrity of transmitted data.
Challenges in Remote IoT Connections
- Network security vulnerabilities
- Limited computational resources on IoT devices
- Scalability issues in managing large IoT networks
Setting Up an Ubuntu Server
Ubuntu is a popular Linux distribution widely used for server applications due to its stability, security, and ease of use. Setting up an Ubuntu server is the first step in establishing a secure IoT environment. Follow these steps to install and configure your Ubuntu server:
- Download the latest Ubuntu Server ISO from the official website.
- Install the ISO on your server hardware or virtual machine.
- Configure the server's network settings and update the system.
Once the server is installed, ensure that it is fully updated by running the following commands:
sudo apt update && sudo apt upgrade
Key Benefits of Using Ubuntu
- Regular security updates and patches
- Wide range of supported applications and services
- Active community support and extensive documentation
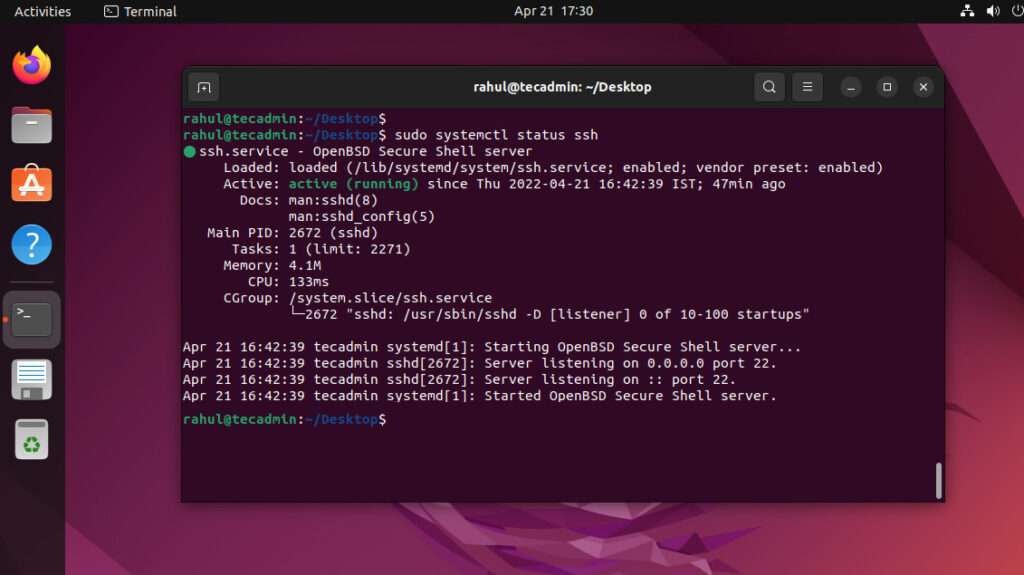
Configuring SSH for Remote Access
After setting up your Ubuntu server, the next step is to configure SSH for remote access. By default, SSH is installed on Ubuntu servers, but you may need to enable and configure it to suit your needs.
Enabling SSH on Ubuntu
To enable SSH, follow these steps:
- Install the OpenSSH server package: sudo apt install openssh-server
- Start the SSH service: sudo systemctl start ssh
- Enable SSH to start on boot: sudo systemctl enable ssh
Configuring SSH Settings
The SSH configuration file is located at /etc/ssh/sshd_config. Open this file with a text editor and modify the following settings:
- Port: Change the default port (22) to a custom port for added security.
- PasswordAuthentication: Set to "no" to disable password-based authentication.
- PermitRootLogin: Set to "no" to prevent root login.
Securing Your SSH Connection
Securing your SSH connection is essential to protect your IoT devices from unauthorized access. Implement the following best practices to enhance security:
Use Public-Key Authentication
Public-key authentication eliminates the need for passwords, reducing the risk of brute-force attacks. Generate a key pair using the ssh-keygen command and copy the public key to your server:
ssh-copy-id user@server-ip
Disable Root Login
Disabling root login prevents attackers from gaining administrative access to your server. Modify the PermitRootLogin setting in the SSH configuration file to "no".
Implement Firewall Rules
Use a firewall to restrict access to your SSH port. For example, you can use ufw (Uncomplicated Firewall) to allow connections only from trusted IP addresses:
sudo ufw allow from trusted-ip to any port custom-port
P2P SSH Connection for IoT
Peer-to-peer (P2P) SSH connections allow IoT devices to communicate directly without relying on a central server. This approach reduces latency and improves scalability, making it ideal for large IoT networks.
Setting Up P2P SSH
To establish a P2P SSH connection, follow these steps:
- Configure SSH on both devices.
- Exchange public keys between the devices.
- Test the connection using the ssh command.
Benefits of P2P SSH
- Reduced dependency on central servers
- Improved performance and reliability
- Enhanced security through direct communication
Best Practices for Secure Connections
Adopting best practices is crucial for maintaining secure IoT connections. Follow these guidelines to ensure the safety of your network:
Regularly Update Systems
Keep your server and IoT devices up to date with the latest security patches and updates. Regular updates help mitigate vulnerabilities and protect against emerging threats.
Monitor Network Activity
Implement network monitoring tools to detect and respond to suspicious activities. Regularly review logs and alerts to identify potential security breaches.
Use Strong Authentication Mechanisms
Enforce strong authentication methods, such as multi-factor authentication (MFA), to enhance security. Combine public-key authentication with additional verification steps for added protection.
Troubleshooting Common Issues
Despite taking precautions, issues may arise when setting up SSH connections. Here are some common problems and their solutions:
Connection Refused
If you encounter a "Connection refused" error, ensure that the SSH service is running and that the correct port is open in your firewall settings.
Authentication Failed
Authentication failures may occur due to incorrect keys or misconfigured settings. Verify that the public key is correctly copied to the server and that the SSH configuration file is properly set up.
Monitoring and Maintenance
Continuous monitoring and maintenance are essential for maintaining a secure IoT environment. Implement the following practices:
Regular Audits
Conduct regular audits of your SSH configurations and network settings to identify and address potential vulnerabilities.
Backup Configurations
Regularly back up your SSH configuration files and server settings to ensure quick recovery in case of failures or breaches.
Conclusion and Next Steps
Securing remote IoT connections through SSH on an Ubuntu server is a critical step in protecting your IoT ecosystem. By following the best practices outlined in this guide, you can establish a robust and secure P2P SSH connection for your IoT devices.
We encourage you to take action by implementing these security measures and sharing your experiences with the community. Leave a comment below or explore our other articles for more insights into IoT security.
Call to Action: Secure your IoT network today by configuring SSH on your Ubuntu server. Share this article with your colleagues and stay tuned for more updates on IoT security!
- Old Bollyflix Rediscovering The Magic Of Classic Bollywood Movies
- Russell Crowe A Detailed Exploration Of The Iconic Actors Life And Career