In today's interconnected world, securely connect remote IoT P2P SSH Raspberry Pi free has become a crucial requirement for both hobbyists and professionals alike. The rise of IoT devices has made it essential to ensure that communication between devices is secure and efficient. As more people turn to Raspberry Pi for their projects, understanding how to establish secure connections is vital for protecting sensitive data.
Imagine being able to control your smart home devices from anywhere in the world without worrying about unauthorized access. By leveraging SSH (Secure Shell) and peer-to-peer (P2P) connections, you can create a robust and secure network that allows seamless interaction between your IoT devices. This guide will walk you through the process step-by-step, ensuring your setup is both secure and cost-effective.
Whether you're a beginner or an experienced user, this article will provide you with the tools and knowledge needed to establish a secure connection for your IoT projects using Raspberry Pi. Let's dive in and explore how you can achieve this without breaking the bank.
- Mastering Remote Iot P2p Download The Ultimate Guide
- Bruce Willis Debunking The Rumors Ndash Did Bruce Willis Die
Table of Contents
- Introduction to IoT and Raspberry Pi
- Understanding SSH Basics
- What Are P2P Connections?
- Raspberry Pi and IoT Integration
- Addressing Security Concerns
- Step-by-Step Setup Process
- Tools and Software Needed
- Optimizing Your Connection
- Troubleshooting Common Issues
- Conclusion and Next Steps
Introduction to IoT and Raspberry Pi
The Internet of Things (IoT) has revolutionized the way we interact with technology, enabling devices to communicate and share data seamlessly. At the heart of many IoT projects lies the Raspberry Pi, a versatile and affordable single-board computer. By securely connect remote IoT P2P SSH Raspberry Pi free, users can harness the full potential of their devices while maintaining robust security measures.
Why Choose Raspberry Pi for IoT Projects?
Raspberry Pi offers several advantages for IoT enthusiasts:
- Cost-effective and widely available
- Highly customizable and compatible with various sensors
- Strong community support and extensive documentation
- Capable of running lightweight operating systems
Understanding SSH Basics
SSH, or Secure Shell, is a cryptographic network protocol that allows secure communication between devices over an unsecured network. When you securely connect remote IoT P2P SSH Raspberry Pi free, SSH ensures that your data remains encrypted and protected from unauthorized access.
- Sd Movie Point Download Your Ultimate Guide To Legal And Secure Movie Downloads
- Hayley Atwell A Rising Star In The World Of Entertainment
Key Features of SSH
- Encryption of data during transmission
- Authentication mechanisms to verify device identities
- Support for secure file transfers
What Are P2P Connections?
Peer-to-peer (P2P) connections eliminate the need for a central server, allowing devices to communicate directly with each other. This approach can significantly reduce latency and improve efficiency in IoT setups. By integrating P2P connections with SSH, you can create a secure and reliable network for your Raspberry Pi-based projects.
Benefits of P2P in IoT
- Reduced dependency on centralized servers
- Enhanced privacy and security
- Improved scalability for large-scale deployments
Raspberry Pi and IoT Integration
Raspberry Pi's compatibility with IoT devices makes it an ideal choice for creating secure connections. By leveraging its processing power and connectivity options, users can seamlessly integrate various sensors and actuators into their projects.
Popular IoT Applications for Raspberry Pi
- Smart home automation systems
- Environmental monitoring solutions
- Industrial automation and control
Addressing Security Concerns
As the number of IoT devices grows, so does the risk of cyber threats. To securely connect remote IoT P2P SSH Raspberry Pi free, it's essential to implement robust security measures. This includes using strong passwords, enabling firewalls, and regularly updating software.
Best Practices for IoT Security
- Use unique and complex passwords for each device
- Enable two-factor authentication whenever possible
- Regularly update firmware and software to patch vulnerabilities
Step-by-Step Setup Process
Setting up a secure connection for your IoT devices involves several key steps. Below is a comprehensive guide to help you achieve this:
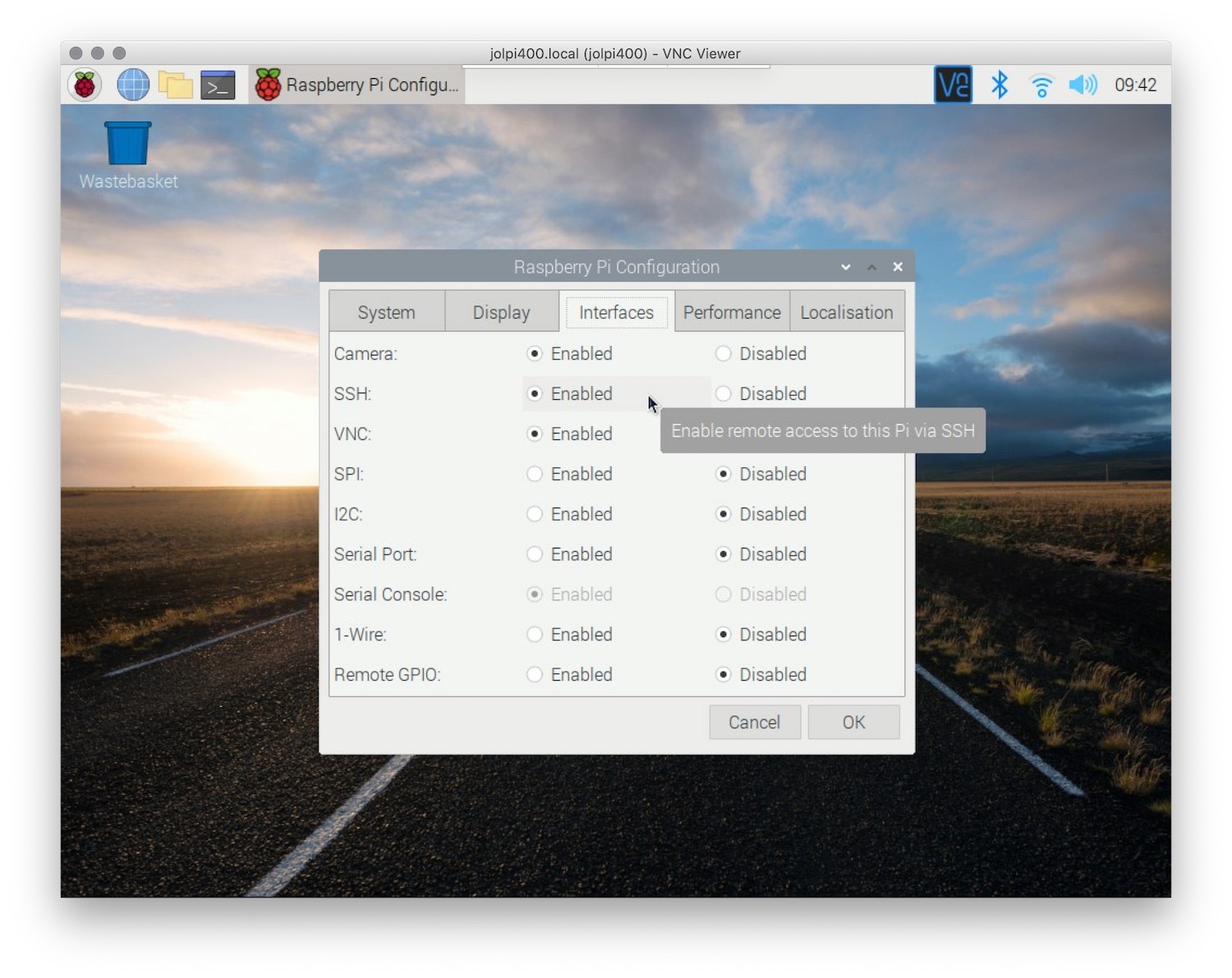
Step 1: Install and Configure SSH
Begin by enabling SSH on your Raspberry Pi. This can be done through the Raspberry Pi Configuration tool or by editing the SSH configuration file.
Step 2: Establish P2P Connectivity
Use a P2P software solution, such as WireGuard or OpenVPN, to facilitate direct communication between devices.
Step 3: Test and Optimize
Once your setup is complete, test the connection to ensure it is functioning as expected. Make any necessary adjustments to optimize performance.
Tools and Software Needed
To securely connect remote IoT P2P SSH Raspberry Pi free, you'll need the following tools and software:
- Raspberry Pi board
- SSH client software (e.g., PuTTY)
- P2P networking software (e.g., WireGuard)
- A reliable internet connection
Optimizing Your Connection
Once your setup is operational, there are several ways to enhance its performance and security:
Tips for Optimization
- Monitor network traffic to detect potential threats
- Use load balancing techniques to distribute traffic evenly
- Regularly review and update security protocols
Troubleshooting Common Issues
Even with the best-laid plans, issues can arise. Below are some common problems and their solutions:
Problem: Unable to Connect via SSH
Solution: Verify that SSH is enabled on your Raspberry Pi and ensure that your network settings are correct.
Problem: Slow Connection Speeds
Solution: Check your internet connection and consider upgrading your hardware if necessary.
Conclusion and Next Steps
In conclusion, securely connect remote IoT P2P SSH Raspberry Pi free is not only achievable but also highly beneficial for protecting your data and enhancing your projects' functionality. By following the steps outlined in this guide, you can create a secure and efficient network that meets your needs.
We encourage you to share your experiences and insights in the comments section below. Additionally, feel free to explore other articles on our site for more tips and tricks related to IoT and Raspberry Pi projects. Together, let's build a safer and smarter future!
Data Sources:
- Bollyflix Spy Unveiling The Secrets Of Bollywoods Hidden Gem
- 4hub Movie Your Ultimate Guide To Streaming And Downloading Movies